g. Opt - Create an IAM Role
These steps are optional and if you have extra time. Please consider moving to Lab I.
You will encounter an issue with permissions now! But, that’s normal this section explains why.
Access to resources by users and services is controlled by Identity and Access Management (IAM). For example, IAM permissions can be added to a policy then a role which can be attached to a user user, group role (admins, devops) or a service (Amazon EC2 to access Amazon S3, Amazon Lambda to access Amazon SQS). For an in depth introduction, see the AWS Identity and Access Management User Guide.
Now that you have created an EC2 instance and logged into the instance using SSH, you can use the instance to access the Amazon S3 bucket created previously.
aws s3 ls s3://bucket-#YOUR_BUCKET_POSTFIX/ # <- use the postfix generated in previous steps
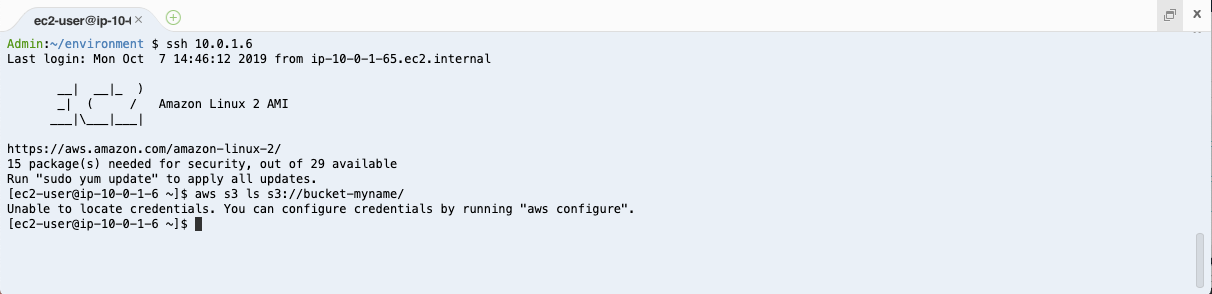
It appears that your instances has not been granted permission to access your Amazon S3 storage. Your AWS Cloud9 instance was granted permissions to some services. However, your new Amazon EC2 instance has not been given any permissions. The next step is to grant the EC2 instance access to S3.
Create an IAM Role for Amazon EC2
Create a role so that your Amazon EC2 instance can access your S3 bucket.
- In the AWS Management Console, choose Services, then IAM.
- In the IAM Dashboard, in the left pane, choose Roles, then choose Create Role.
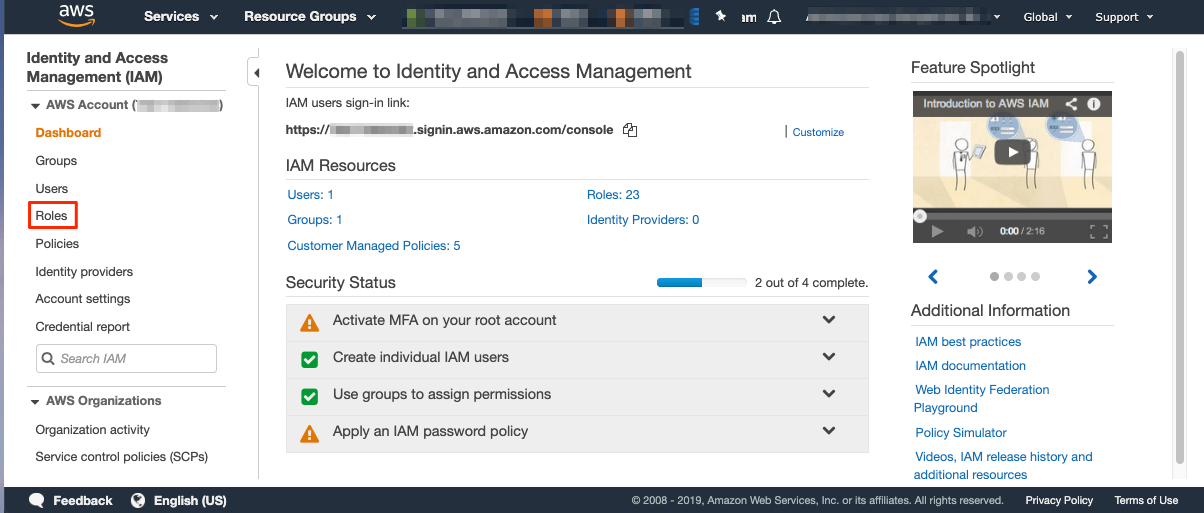
- For Select type of trusted entity, choose AWS Service.
- For Choose the service that will use this role, choose EC2, and then choose Next: Permissions.
- In the search field, type S3 and choose the AmazonS3FullAccess policy to provide full Amazon S3 access for your Amazon EC2 instance.
- Choose Next: Tags and leave the default settings.
- Choose Next: Review.
- Type a Role Name, such as S3FullAccessForEC2, then choose Create Role.
Your role is now created. Search for your role S3FullAccessForEC2. Selec the role to take a detailed look at the new role and policy. Select the Trust Relationships tab and you can see that Amazon EC2 is one of the trusted policies (meaning it can use this role).
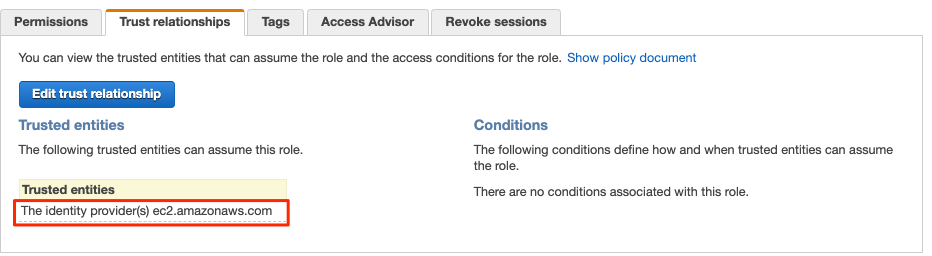
Select the Permissions tab and expand the AmazonS3FullAccess policy. Then, select {}JSON. You should see the permissions below. These permissions are open because they allow your Amazon EC2 instances to conduct any action on Amazon S3.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*"
}
]
}
However, you can also restrict these permissions to only some actions, such as List or Put, to be conducted on a particular Amazon S3 bucket. For example:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": [
"arn:aws:s3:::bucket-myname",
"arn:aws:s3:::bucket-myname/*"
]
}
]
}
Note that full access to Amazon S3 is acceptable in the context of this workshop but fine-grained control is highly recommended for anything other than temporary sandbox testing.
IAM is a great way to control who and what can access which resources at a fine level of granularity. To learn more about IAM policies and the IAM Policy Simulator, see Testing IAM Policies with the IAM Policy Simulator.
Attach the IAM Role to an Amazon EC2 Instance
Now that you have created a new IAM role, you can assign it to your EC2 instance:
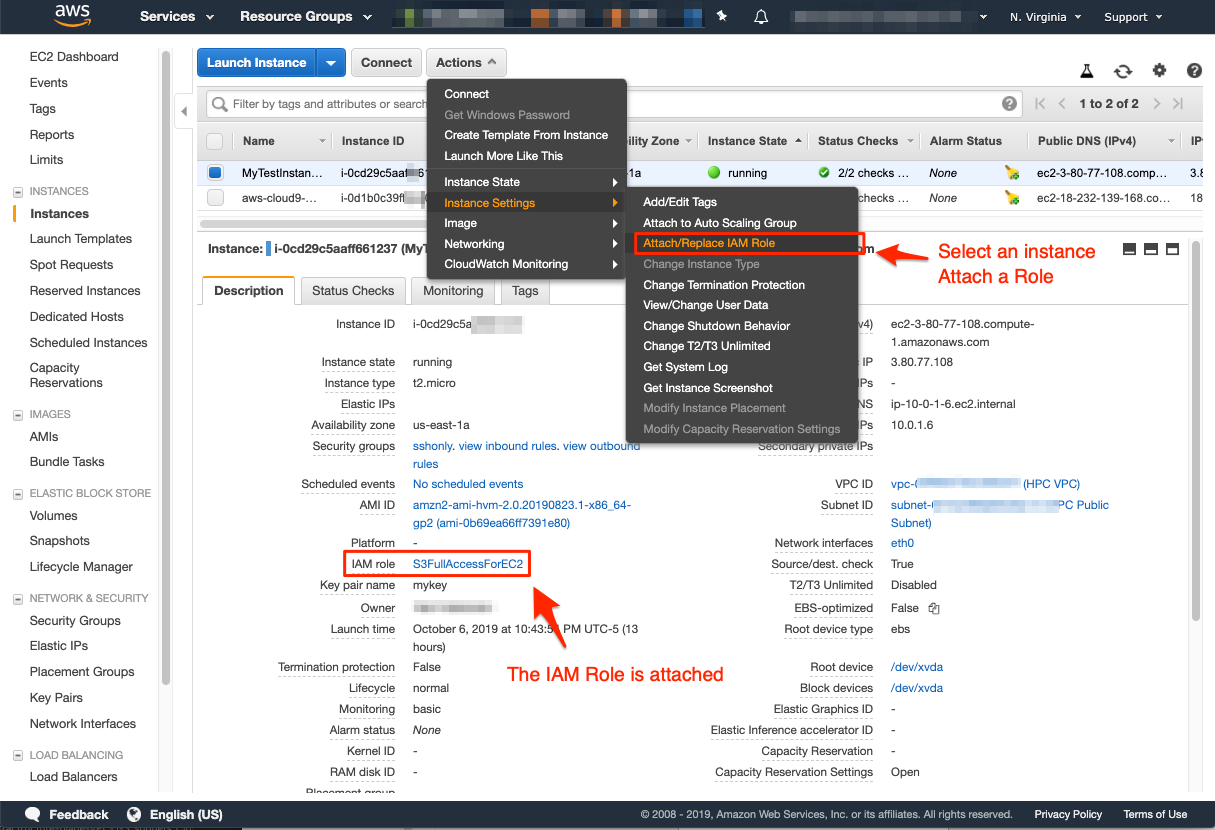
- Navigate to the EC2 Dashboard then choose Instances.
- Choose your instance, then choose Actions, Instance Settings, and Attach/Replace IAM Role.
- Select the newly created IAM Role, and choose Apply. Your role is attached and visible in your EC2 instance details. Your EC2 instance is now allowed to access S3.
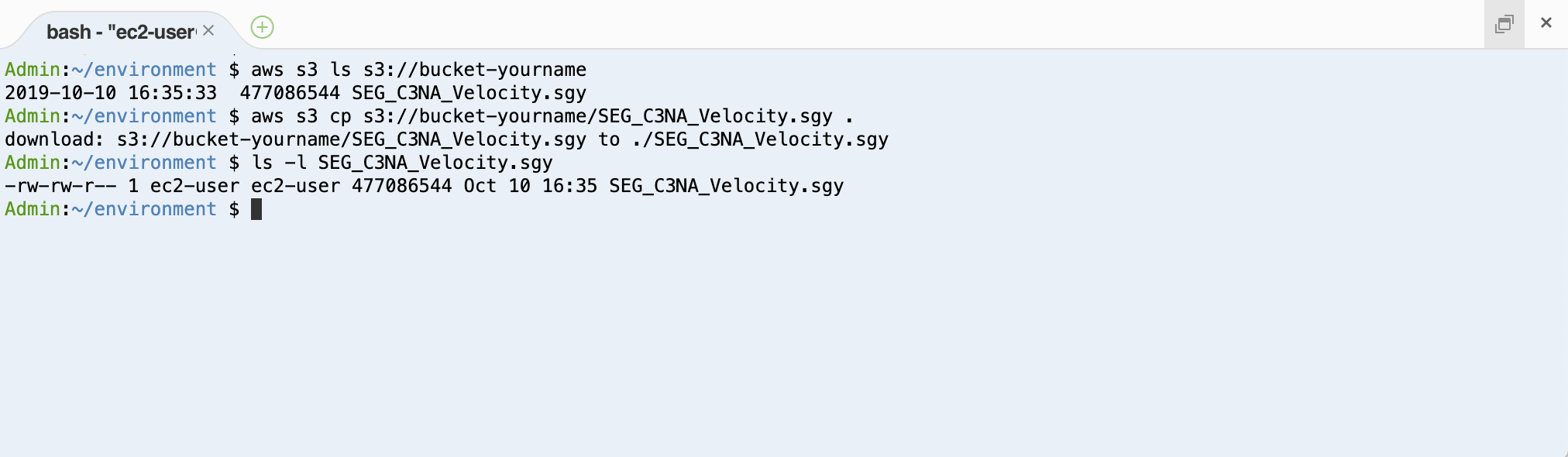
- Return to your AWS Cloud9 IDE, connect to the instance with SSH, and run the following commands (don’t forget to change the bucket name to yours!). This command lists your Amazon S3 bucket content then downloads the file downloaded previously.
aws s3 ls s3://bucket-${BUCKET_POSTFIX}/
aws s3 cp s3://bucket-${BUCKET_POSTFIX}/SEG_C3NA_Velocity.sgy .
ls -l
You should see a result similar to the example shown in the following image.